For several years I’ve occasionally logged onto Shodan and searched for Minecraft servers. I just join, look around, and maybe leave a sign for the server owner. I’d also occasionally heard stories about people making their own Minecraft server scanners.
A while ago, on April 1st 2022, cybersecurity YouTuber LiveOverflow uploaded a video titled “I Spent 100 Days Hacking Minecraft”. Despite being uploaded on April Fools’, the video and series that followed was actually really interesting. Anyways, after a bit I got the idea of searching for “liveoverflow” on Shodan. To my surprise, the server actually showed up and even more surprisingly it wasn’t whitelisted. There were signs at spawn that congratulated you but said “I hope you built a tool yourself”. I had not built a tool myself.
A few weeks later, Minecraft documentary YouTuber TheMisterEpic uploaded a video about “Minecraft’s most dangerous glitch”. Spoiler: The bug in the video is not dangerous. I wanted to let TheMisterEpic know, so I joined his Discord and pinged him in general chat. Some people were disagreeing with me, but a member in the server named Ada came to my defense. We talked a bit and another server member named Gildfesh told me how him and Ada developed Minecraft hacks and had recently released a mod for faking Minecraft chat reports. Later, a member named Shrecknt brought up LiveOverflow’s Minecraft YouTube series. This made me start thinking about it again, so I decided to rejoin the server once again. This time, there was a player online. We talked a bit, and they invited me to a Discord server named “Server Scanning Inc”. Everyone in the server was super cool, and coincidentally Ada and Gildfesh also happened to be members here.
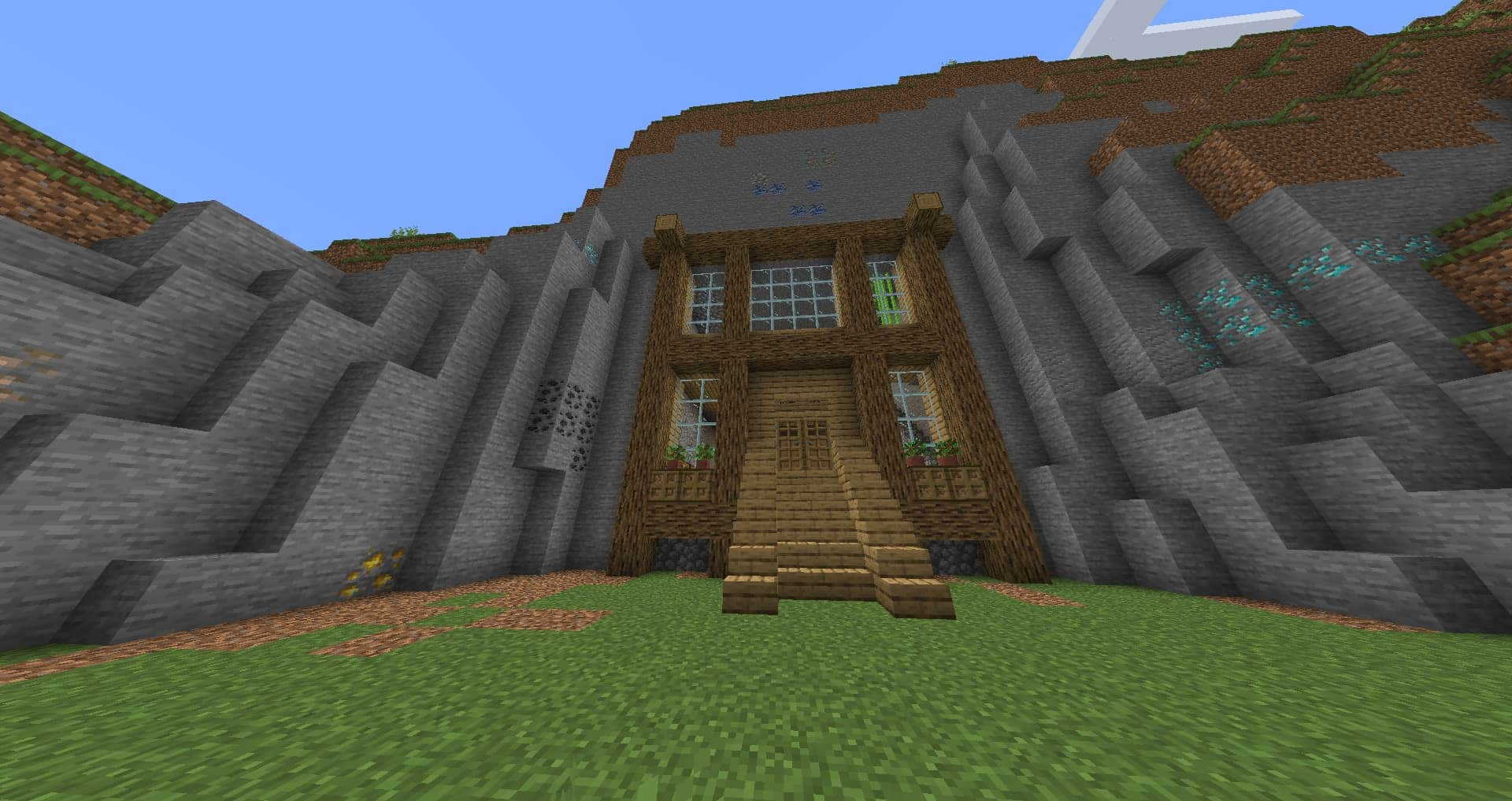
I grinded on LiveOverflow’s Minecraft server for the next few days, building a house, acquiring good tools, building some infrastructure in the Nether, and making an underground potato farm. For fun, I set up a website that tracked Hermitcraft player activity and made a honeypot Minecraft server using node-
Making a scanner
I got jealous of how everyone in the server had their own scanner and I cheated by using Shodan, so I decided to scan the internet myself. I already knew of masscan, which lets you send TCP SYN packets to every IPv4. Masscan also has support for getting basic banner data of various protocols such as HTTP and SSH, but it didn’t have support for pinging Minecraft servers, so I decided to attempt to add it myself. Unfortunately, masscan is written in C and I have very little experience in C. While trying to write the code, I remembered Bithole’s blog post about scanning the internet for Minecraft servers so I went to re-
I already had a VPS on Oracle Cloud, which gives you a free “forever” powerful server, so I ran the masscan fork on it. There were several issues. First, it took several hours to scan as opposed to the 5 minutes I was led to believe it would take. Second, it was missing most servers which I expected to be there. Third, when I searched for my honeypot in the results, there were several servers that looked like they had the same MOTD as my honeypot but had different IP addresses.
For the first issue, I learned that the “millions of packets per second” advertised by masscan only applies to dedicated machines that weren’t virtualized. I also tried installing PF_
The second issue was a much bigger deal: Oracle Cloud was dropping packets. When I scanned at lower rates, I got less dropped servers, but also I didn’t want to scan at lower rates. I found I could get Oracle to drop less packets by making the firewall rules stateless, but the amount of dropped packets continued to be unacceptable. I’d have to switch to a different host.
The third issue was a bit annoying, and I found out it was happening because crazy people decided to make “mirror” servers that open TCP connections with you and send you everything you send them, so they ended up pinging my honeypot (which was on the same server as my scanner) when I scanned them. This would stop being an issue once I switched hosts.
My current design for my scanner runs on two servers. The first server has a Python script that hosts a Discord bot and automatically executes masscan commands that pipe into another Python script that uploads to my database. The second server has a Cron Job that executes every hour that runs a custom scanner I made in Rust that checks every alive server that’s already in my database, and pipes that output to the same script used for uploading my masscan results. I also store players that were previously online into my database so later I can search for servers that players frequent.
Trying Hosts & Complaints
Since Oracle Cloud was dropping packets, I had to find a different host to do my server scanning on. First, I tried Google Cloud, but they shut down my instance after a couple of days for “abnormal activity”. Then I tried Azure, but their website was broken and didn’t let me use my free credits. After those, I decided to try Linode. I’d heard people recommend Linode for scanning, so I thought it’d be fine, And it was, for about two weeks. I occasionally received abuse complaints on Linode, but I just replied to them telling them that I was simply scanning the internet for Minecraft servers and everything I was doing is legal. I had to do this several times, and they were fine with me, until they decided they weren’t.
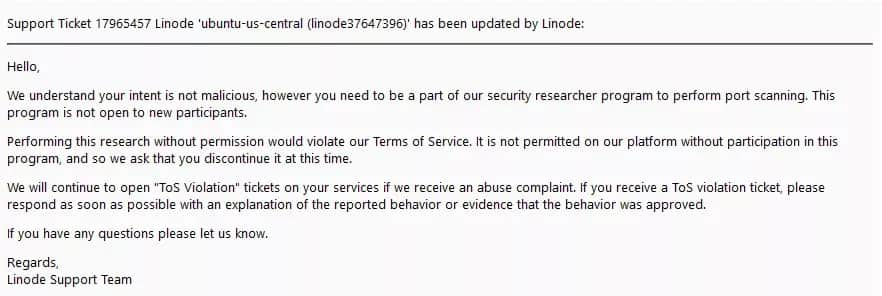
The final abuse complaint was actually sent by Hetzner for some reason, even though I wasn’t using Hetzner for scanning. After being banned from Linode, I deleted my account and went back to searching for a new host for my server scanning. I’d heard from Souper that Scaleway was very good for scanning, so I bought their $2/
One funny thing I encountered early on was a silly little website called AbuseIPDB. Their about page says the website is for “identifying IP addresses associated with malicious activity online”, but from my experience that’s not what it’s used for. Fortunately, reports on AbuseIPDB are purely cosmetic and don’t actually do anything other than serve as a fun leaderboard. At the time of writing, my primary scanning IP has 769 reports and I have friends with thousands of reports, despite doing nothing other than sending SYN packets to a few IP addresses.
Bots
So remember that underground potato farm I made on LiveOverflow’s server? I could obtain about 1 inventory’s worth of potatoes per 30 minutes-

I also decided to make the bot bridge in-
Honeypots
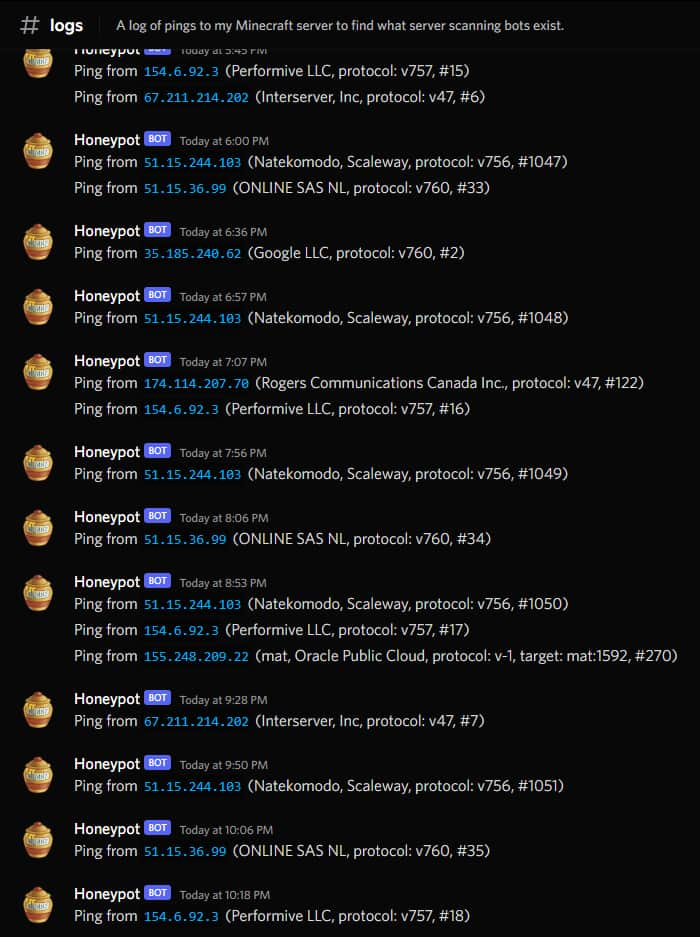
I briefly mentioned my honeypot server earlier, how it uses node-

I also gave the source code for my honeypot to some friends, and they modified it and set it up on their own servers. A member named Cleo made a really cool honeypot that proxies traffic from the honeypot to the real server, but logging the players who join and adding some fake disconnections and lag to troll the people using them. At the time of writing, there’s 6 alive servers named “LiveOverflow Let’s Play”. There was also some drama that happened when a member decided to fill up the server with bots to prevent people from joining, but I’m not going to get into that here.
Conclusion
There were some other fun things that happened, such as:
- Me realizing that Docker Minecraft Server has “minecraft” as the default RCON password (though I only found a few hundred servers with the port open with that password)
- Me making a Minecraft server for exploring servers in my database by entering doors in an infinite hallway.
- SushiPython and I confusing a lot of random Minecrafters by joining their servers.
- Me making a bot that joined every 1.19.2 offline mode server and tried joining as past usernames until it found an admin.
If you read this entire blog post, I encourage you to make your own server scanner and have your own adventures. As a little sendoff, here’s a few completely random servers from my database for you to explore:
If you want more, make your own scanner. See you next time, when I decide to publish another blog post in two years ;)